Cryptocurrency wallet development has become one of the pillars of the expanding crypto industry. The growing acceptance of virtual assets throughout the world has led to a tremendous surge in demand for secure and easy-to-use crypto wallets. This guide will help you navigate the intricacies of crypto wallet application development from scratch. From conceptual knowledge to the application of that knowledge to develop a top-notch cryptocurrency wallet, we have got you covered.

We will discuss the different types of crypto wallets such as hot wallets, cold wallets, as well as hardware wallets. You will learn how to develop a Bitcoin wallet and a crypto wallet app for other cryptocurrencies. We will also provide you with detailed insights into the main blockchain wallet development elements. As we all know, security is of the essence in using and holding cryptocurrencies. We will discuss such inseparable from the crypto world elements as the role of private keys and public keys in protecting your virtual money as well as biometric authentication. Moreover, we will provide you with a detailed explanation of the use of artificial intelligence to enhance the security of your wallets and effectively respond to cyber threats.
By the end of this article, you will have a sound understanding of the way cryptocurrency wallets work and will be ready to put your newly acquired knowledge to practical use. Be it a professional software developer or an average ‘Joe’ fond of the crypto topic, this article will offer both valuable theoretical insight and practical advice. Let us get started!
Types of Crypto Wallets: Choosing the Right Digital Safe

A cryptocurrency wallet is a digital interface that secures the cryptographic keys required to access one’s digital assets on the blockchain. Unlike a traditional wallet that carries the physical currency, the crypto is a digital account.
There are various types of crypto wallets, each with its merits and security drawbacks.
Types of Hot Wallets
The hot wallet is ideal for traders who need access to an exchange or other cryptos without any hassle on the go. However, due to an always-on internet connection, hot wallets are nearly always simple.
Types and Examples
- Mobile Wallets: These apps are applications installed on your smartphone. They are convenient to use and carry. Examples include Coinbase Wallet and Trust Wallet.
- Web Wallets: These wallets are accessed through a web browser. They mitigate the concerns associated with platform centralization, although security relies on the browser used. Examples include MetaMask and Binance Wallet.
- Desktop Wallets are installed on a computer, providing the end-user more control. Although they are not as easily accessible as mobile wallets, they are quite convenient. Examples include Electrum and Exodus.
Additional Security Measures to Mitigate the Risks
There are ways to manage the associated risks, as will be highlighted below:
- Two-factor authentication (2FA): You either receive an SMS with an authorization code or access to your e-mail, making it mandatory.
- Strong passwords: It is essential to use a unique and hard password for each service.
- Regular updates must be carried out.
- Beware of phishing attacks that are likely to try to steal user names and passwords.
Hot wallets are ideal for convenience; however, the security measures mentioned will help mitigate the risks associated with such.
Cold Wallets: The Highest Level of Security
Cold wallets, which are offline and not connected to the internet, are the most secure way to store your cryptocurrencies. Although less convenient than hot wallets, cold wallets are suitable for storing significant sums of money.
Types of Cold Wallets
- Paper Wallets: A printed form of your public and private keys, a paper wallet provides perfect security but has poor physical resistance guarantees
- Hardware Wallet: With offline and physical storage of your cryptocurrency’s private keys, a hardware wallet provides the same high level of security but is not fraught with the drawbacks of a paper wallet. The most popular options are Ledger Nano S and Trezor Model T.
Security Measures for Cold Wallets
In order to securely store your cold wallet, you need to:
- Create multiple backups of your paper wallet and, very importantly, the recovery seed of a hardware wallet. Since because the storage device is not connected to the internet, we can not reinstall the crypto wallet in an emergency; we can only make a new cold wallet and claim it to be the previously existing one by revealing the recovery seed to the system.
- Store your cold wallet, preferably a hardware wallet, in a physically inaccessible place, as someone who gets access to your cold wallet can use it later rather than you. Thus, it should be kept in a vault or a bank safe.
- Verify the authenticity of your hardware wallet to avoid counterfeit devices. Either buy a hardware wallet from the producer directly or very methodically verify the source of the wallet you buy to avoid purchasing a poorly fabricated counterfeit.
By following these guidelines, you can significantly reduce the risk of unauthorized access to your cryptocurrencies.
Hardware Wallet: The Gold Standard of Crypto Security
Hardware wallets are a type of a cold wallet, which ensures an exceptional level of security. These are devices that physically protect your private key. For these reasons, hardware wallets are a popular choice for substantial crypto assets.
Key features and benefits:
- Offline storage: the device’s being offline is fundamentally secure against hacking.
- Pin code: a hardware wallet is more secure thanks to an additional protection measure.
- Backup options: Most hardware wallets offer the ability to generate a recovery seed, which is a sequence of words that you enter if the device is lost.
- Compatibility: Many hardware wallets support a wide range of cryptocurrencies.
Although a hardware wallet may be the most securely protected type of a crypto wallet, it may not be the most convenient one due to its being a physical device. However, learning the key features and unsafe wallet behaviours allows making an informed choice.
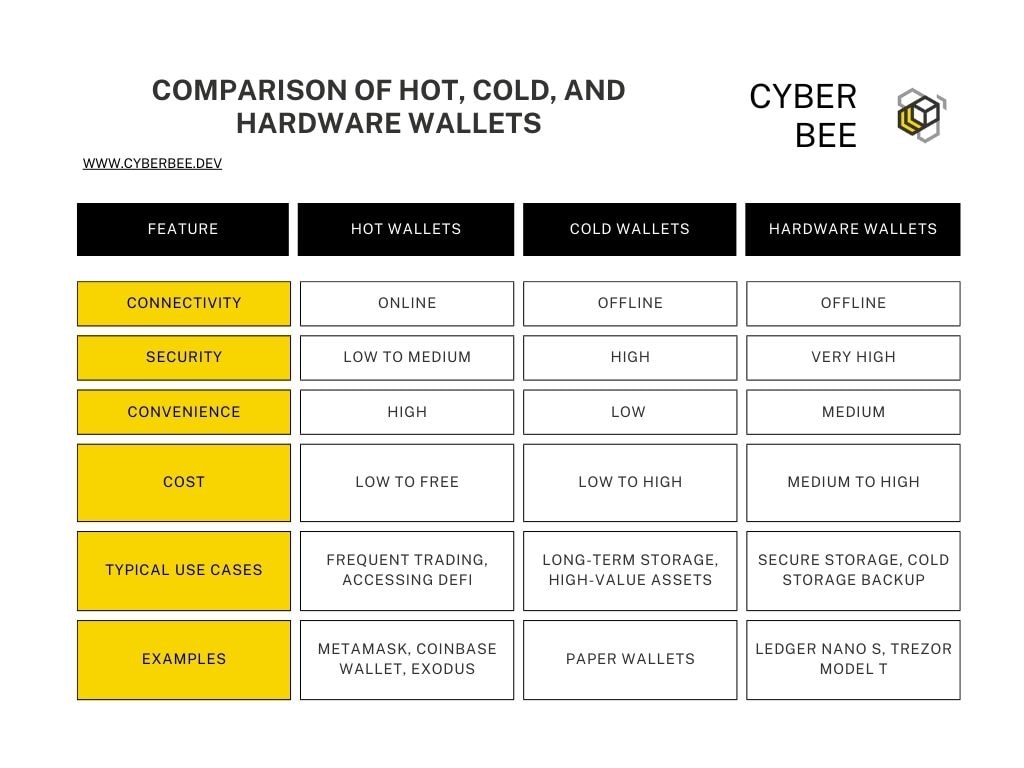
Note: Security levels are relative and may vary depending on the implementation. Hardware has an additional layer of physical security compared to cold storage, such as paper wallet.
This table provides a clear overview of the key differences between hot, cold, and hardware wallets, helping you make informed decisions based on your security and convenience needs.
Step-by-Step Guide to Your Own Crypto Wallet Development
Breakdown of the Essential Elements
More than just a digital vessel, crypto wallets contain so much more. It is an intricate system built on many building blocks:
- Private keys: these are the cryptographic codes that establish you as the sole owner of your cryptoassets. It is crucial to secure these keys.
- Public keys: Derived from private, public keys are used to receive payments in cryptocurrency. They can be safely shared out publicly.
- Wallet addresses: A more easily readable version of a public key that are used to send and receive cryptocurrencies.
- Blockchain interaction: The wallet should provide support for interfacing with the desired blockchain network, to broadcast and verify transactions.
- User interface (UI) and user experience (UX): Looking at the user interface (UI) and experience this is all about supporting users in their needs as do well designed wallets we promise to include a wallet with multi-currency support, your transactions history, Scan/ read QR Code securely.
The Development Process
Crafting a successful crypto wallet app involves a deliberate approach, thoughtfully incorporating sophisticated technological aspects:
- Market Research and Target Audience Identification: Grasping the intended demographic is pivotal for tailoring the crypto wallet to explicit user demands. Conduct extensive market research to identify opportunities, barriers, and competitive landscapes.
- Technology Stack Selection: Choose programming languages and blockchain progress frameworks that align with venture aims. Consider leveraging pre-built crypto wallet libraries to accelerate progress while preserving code quality and security.
- Architecting the Wallet: Determine the optimal wallet type (hot, cold, hardware, or software) founded on security, accessibility, and target user demands. Design the underlying building, prioritizing security, scalability, and user journey. Implement robust security steps like encryption, authentication, and key management from the inception.
- Smooth Blockchain Integration: Select blockchain networks that align with the crypto wallet’s target audience and functionalities. Decide whether to run a full node or rely on a lightweight client, considering factors like security, performance, and decentralization. Effectively integrate with blockchain APIs for real-time data and transaction management. Explore scalability solutions like Layer-2, sharding, or sidechains to accommodate growing user bases and transaction volumes.
- Prioritizing Security: Implement advanced security protocols like AES, RSA, or ECC encryption to protect sensitive data. Employ robust key management practices for secure generation, storage, and recovery. Conduct regular security audits and penetration testing to identify vulnerabilities proactively. Consider hardware security modules (HSMs) for enhanced protection of cryptographic keys.
- Leveraging Development Tools and Frameworks: Utilize blockchain SDKs to streamline development and integration with specific platforms. Explore open-source wallet libraries for pre-built components, but carefully evaluate their security and compatibility. Consider cross-platform progress frameworks like React Native or Flutter to reach a wider audience. Leverage cloud infrastructure for scalability, cost-efficiency, and reliable performance.
- Designing the User Experience: Create an intuitive and visually pleasing interface that prioritizes clarity and simplicity. Incorporate essential features like transaction history, balance outline, and QR code scanning. Gather user feedback throughout the progress process to refine the user experience.
- Core Functionality and Feature Development: Implement fundamental features such as sending, receiving, and storing cryptocurrencies. Explore additional functionalities like staking, swapping, and DeFi integration based on target market demands. Ensure seamless integration with various blockchain networks to expand the crypto wallet’s utility.
- Security and Privacy by Design are perhaps the highest priorities for this project, leading to the need to incorporate robust security measures from the very beginning. As it was already mentioned, supporting strict privacy regulations and ensuring measures for protecting users’ data are also crucial. In addition to that, it is also advisable to maintain regular security audits and updates to tackle any new threats that might be encountered.
- Rigorous Testing and Deployment should also be considered, with developers having to test their wallet at every appropriate level. Beta testing is an excellent tool for gathering user feedback and supporting iterative improvements, while deploying the wallet on relevant platforms is an inseparable part of the process.
integrate these steps and address the abovementioned technological considerations during the development of your crypto wallet tcreate robust, secure, and user-centric cryptocurrency wallets.
Key Challenges and Considerations in Cryptocurrency Wallet Development
Developing a successful cryptocurrency wallet requires overcoming a range of complex challenges.

Trust Is Enabled By Security
Above all else, the imperative is to protect user funds. Trust is all you have, so it goes without saying that online security needs to be incredibly secure.
- Advanced Encryption: Using the most up-to-date encryption technology available, like AES/RSA/ECC, to secure confidential data.
- Robust Key Management: Enables secure key generation, storage and recovery mechanisms.
- Regular Security Audits: Security assessments and penetration testing to ensure no holes in the whole system.
- Bridging Hardware (HSM): Envisioning HSMs for Further Secured Cryptographic Key Defense
- Multi-Factor Authentication (MFA): Clients should furnish at any rate two more sorts of evidence that they are the individual they contend to be so as to get entrance into their record.
- Cold Storage Integration: For storing cryptocurrency offline and reducing risks to integrate various cold storage solutions.
User Experience: Driving Adoption
Attracting and keeping users depends on delivering a user experience that is as smooth and natural to use as possible.
- UI Development Workflow: What and how much of the components/UI elements should be broken down to achieve right level abstraction for an intuitive interface design — focussing on clarity, simplicity etc.
- Onboarding: Building an educational and coherent on-boarding for new users.
- App Support and an educational resource to help users understand what cryptocurrencies and wallet work
- Customer Support: Featuring solid and knowledgeable customer support options.
- Accessibility: Ensuring the wallet is usable by users with disabilities.
Scalability: Handling Growth
The crypto wallet must be capable of scaling efficiently as the number of users and transactions volumes grow.
- Efficiency: Strategies to ensure transaction are performing in less than a second or two.
- Cloud Infrastructure: Use of cloud platforms to achieve scalability and cost optimization.
- Distributed Systems: Made room for distributed architecture to serve high loads.
- Database Optimization – For better and efficient data storing & retrieval.
Compliance and Regulation
Understanding complex regulatory environments is very important for running a profitable crypto wallet business.
- KYC/AML Compliance: Assure a KYC and AML compliant system.
- Data Privacy: Ensuring protection of users’ data is compliant with regulations such as GDPR and CCPA.
- Licensing and Permits: Acquiring all required licenses and permits from the municipalities in which a facility resides.
- Regulatory Monitoring: Keeping abreast of changing regulatory pressures.
Market Competition and Segmentation
With so much noise in the crypto wallet space, a novel value proposition is what stands out.
- Identifying a Niche: Concentrate on single target group or specific features.
- Innovation: Creating the newest features and technology.
- Partnerships: Collaborating with other firms have to reach and capabilities.
- Branding and Marketing: Building a strong brand identity and effective marketing campaigns.
This way by solving the key challenges and considerations. crypto wallet development companies can establish successful ventures, which will be beneficial both to them as well users in terms of long term use cases.
Creating a Cryptocurrency Wallet App: Critical Aspects
In order to build a winning cryptocurrency wallet app, you need mastery in user expectations and dynamism of technology advancements along with the vagaries within crypto space. Let’s delve into the key factors that influence the development of a compelling wallet app.
Understanding the User Journey
Crypto Wallet Build Need to be in a user-centric manner. If we can map the user journey, then by understanding this complexity a natural and seamless experience could emerge.
- Onboarding: You only get one chance to make a great first impression. You need to have a straightforward onboarding process that directs new users easily.
- Security: For most of the users, this is their number one priority. Best practices for deploying more secure infrastructure, including 2FA, biometrics and cold storage solutions.
- Usability: An aesthetic and interactive interface improves user experience. Transaction history, balance overview and QR code scanning should be easily accessible.
- Education: Offer up educational material that helps users to stay informed and engaged. Using guides, glossaries and Market Insight can provide a better user experience.
Core Features of a Cryptocurrency Wallet App
Though the features might differ according to audience expectations and what is trending in the market, a high-quality crypto wallet app will usually consist of these characteristics:
- Wallet creation: generate public and private keys to secure the funds of users.
- Multi-currency support: let the user store and manage more than one crypto.
- Send and receive: Transact with inside the application without any friction.
- Transaction history: Provide a clear record of all transactions.
- Safety measures: Build advanced security systems to secure funds of operators and players alike.
- QR code support: Enable fast transactions using QR code support
- Exchange integration: allow users to buy and sell currencies directly from within your app anywhere.
- Customers: Provide dependable and easily-accessible support avenues
Technical Underpinnings of Crypto Wallet Development

Script programming language is the other pillar for Crypto wallet development. In order to develop a successful cryptocurrency wallet, you have to be very detail-oriented.
- Blockchain integration: Interacting with blockchain networks easily is essential functionality for a wallet. If you would like a more comprehensive article that teaches the ins and outs of how transactions are verified and then added to their respective blockchains, read How is a Transaction Verified on a Cryptocurrency Network?
- Crypto Wallet architecture: Deciding whether you would need hot or cold storage based on security/accessibility needs.
- Security protocols: Implementing strong encryption, key management and protection from all kinds of vulnerabilities.
- Performance optimization: Show you how quick and responsive your app can be even with millions of transactions
- Scalability: code should be written in such a way that it is able to take the growing amount of data and increased user base writelier
Monetization Strategies
There are different strategies that can be employed when it comes to monetizing a cryptocurrency wallet app:
- Transaction Charges: Charging a small fee for each transaction.
- Exchange partnerships: Working with cryptocurrencies for reward fees or revenue splits.
- Premium features: Offering additional features or services for a subscription fee.
- Interest income: based on interest generated through staking or lending of user funds.
- Advertising: Showing targeted ads in the app.
Carefully selecting monetization strategies which respect a user’s experience while also not compromising security or privacy.
Taking these factors into account will enable you to build a top-of-the-line crypto wallet application that easily exceeds the competition, empowering users.
Enhancing Crypto Wallet App Development with Advanced Features
Smart Contracts Integration
Smart contracts, self-executing contracts with the terms of the agreement directly written into code, offer a myriad of possibilities for crypto wallets. By integrating smart contract functionality, wallets can:
- Enhance security: Implement advanced security protocols using smart contracts.
- Expand functionality: Enable in-app DeFi services such as lending, borrowing and trading.
- Create new revenue streams: Build a special tokens, dApps running on the platform of wallet.
To learn more about the costs of smart contract audits, which is a crucial step to secure your smart contracts see here: Smart Contract Audit Cost Explained by Alex Topal, CTO of Cyber Bee.
Decentralized Finance (DeFi) Integration
The cryptocurrency landscape has been transformed by the rise of Decentralized Finance (DeFi). The binance X team stated that integrating DeFi services with cryptocurrency wallet development provides significant benefits to users by enabling new functionalities and revenue opportunities.
- DeFi protocols: Access to a number of different DeFI platforms from the wallet itself
- Yield farming: Allow users to earn rewards staking their assets.
- Liquidity provision: create capacity to users who supply liquidity into Defi pools.
- Decentralized exchanges (DEXs): Integrate DEX functionality for peer-to-peer trading.
Non-Custodial vs. Custodial Wallets
Understanding the distinction between non-custodial and custodial wallets is crucial for crypto wallet development:
- Non-custodial wallets: Offer the best security for your funds as you are in complete control of your private keys but need to have some understanding of how wallets work.
- Custodial wallets: A third party has the private key, making it convenient but less secure.
By offering both options, wallet providers can cater to a wider audience with varying levels of crypto expertise.
Interoperability

The cryptocurrency ecosystem is growing and it started being crucial to have access to different blockchains, from communication with crypto wallets.
- Multi-chain support, that is to manage various kinds of cryptocurrency in different blockchains.
- Cross-chain transactions: Easiest way to transfer assets across networks
- Atomic swaps: Enable direct peer-to-peer exchange of cryptocurrencies without intermediaries.
Wallet Security Best Practices
Security has always been paramount in the crypto wallet apps and implementing robust measures should be a no-brainer. However, in case you’ve already used all the usual techniques, implementing the following options could also be a wise choice:
- Key management strategies: Explore advanced key management. For example, hierarchical deterministic wallets or multi-party computation. Example: Trezor uses the Shamir Secret Sharing Scheme to protect recovery seeds.
- Encryption standards: Make sure to use industry-approved and battle-tested encryption algorithms to protect user’s data.
- Security audits and bug bounties: Regular security assessment and incentivizing ethical hacking could do wonders in enhancing a wallet’s security.
- User education: Make sure to provide your users with concise guidelines on the best practices in securing your wallet.
If you are a crypto wallet app developer, keep in mind that implementing these advanced features and best practices is not very difficult or expensive in most cases. At the same time, they let you stay ahead of the competition and present an innovative and secure product that meets your users’ needs.
Case Studies and Industry Insights
Successful Cryptocurrency Wallet Development Stories
The crypto wallet landscape is populated by numerous players, each with unique strengths and strategies. Let’s examine a few notable examples.
Coinbase Wallet:
The Coinbase Wallet is a non-custodial crypto wallet that has originated as a kind of an extension of the Coinbase crypto exchange. As for this kind of solution, the descriptions can be characterized to be using features of being easy-to-use. In addition to that, the main valuable strength of this kind of crypto wallet is the capability to interact and well-integrate into other parts of the whole environment of such projects.
MetaMask:
The MetaMask crypto wallet was created and developed as a kind of pilot project in the field of the Ethereum ecosystem. It is known as a very practical and comfortable tool for work using the wib-environment format in the function of a browser extension claimed to perform well when interacting with decentralized applications or so-called dAPPS and DeFi platforms.
Ledger:
The Ledger presents a rather specific kind of hardware solutions known as cold storage serving the function of a kind of wallet decreasing greatly the risks of the loss of the assets placed on it. Its distinct and visible advantages are those in the sphere of being secured. The Trust Wallet should be considered the mobile first type of decentralized cryptocurrency wallets and its valuable features are those in the field of usage such as supporting disparate range of all the popular tokens and coins.
Trust Wallet:
Trust Wallet is one of the well-known wallets that has gained its popularity being a mobile-first crypto wallet. In order to increase a user base, the company has decided to support a big number of cryptocurrencies and integrated with Binance. The company has got a competitive advantage by focusing on its decentralization aspect of finance with the development of DeFi. Its customers are increasing nowadays and the investors are interested in the development of this startup.
Examples of the crypto wallets illustrate different approaches to crypto wallet development and thus, shed light on factors contributing to their success. This information will be useful for the developers, who would have a possibility to obtain an insight in the possible ways to enhance their projects.
The Future of Crypto Wallets
Building crypto wallets is a challenging, yet highly rewarding process. Developing secure, user-friendly and, most importantly, scalable wallets requires an in-depth knowledge of blockchain technology, the current cryptocurrency market and its tendencies. Mastering private key management, client and server wallet security and ensuring the necessary level of UX will enable developers to build a crypto wallet app that drives the mass adoption of digital coins.
In the future, smart contract integration and DeFi functionality should become a priority. Staying both behind the curve and ahead of it with the rapidly changing regulations will help crypto wallet development companies avoid stagnation and survive in the long term. To help focus the effort in the right direction, future developers must concentrate on enhancing crypto currency wallet security, improving the quality of wallet user experience and further enhancing them as digital asset storage solutions. As a result, the crypto wallets will become a multi-purpose solution that will help users benefit from its functionality across a variety of platforms. To summarize, crypto wallet app development is crucial to the cryptocurrency ecosystem growth. Sticking to the rules introduced in the paper, developers will grow a high chance to build a wallet solution that satisfies the demand of a dynamically changing market and drives the mass adoption of digital money.



