Front running is a big problem in traditional and crypto markets. In DeFi, where transactions are public before execution, front running is even worse. This article will go over the mechanics of front running, how it affects crypto projects and how blockchain startups can protect themselves from such attacks.

Front running is a big problem in traditional and crypto markets. In DeFi, where transactions are public before execution, front running is even worse. This article will go over the mechanics of front running, how it affects crypto projects and how blockchain startups can protect themselves from such attacks.
Understanding Front Running in Crypto
Front running occurs when someone executes a trade based on prior insider knowledge of an upcoming transaction that is likely to influence asset prices. In traditional finance, this typically involves brokers leveraging confidential client order information to gain an advantage. In the crypto space, it takes the form of bad actors exploiting the transparency of blockchain transactions to place their own trades ahead of others, profiting from the resulting price changes.
Unlike conventional markets, where strict regulations enforced by organizations like the Financial Industry Regulatory Authority (FINRA) prohibit such practices, decentralized exchanges (DEXs) function on open ledgers. This transparency presents new opportunities for front running, often carried out by automated bots or miners manipulating transaction ordering.
How Front Running Works on the Blockchain
 Bitcoin mempool
Bitcoin mempool
In the crypto ecosystem, front running happens because transactions are visible on the blockchain before they are finalized. This openness allows malicious actors (bots or miners) to monitor the mempool – a space where pending transactions wait to be processed. By spotting large or price-sensitive trades in the mempool, they can place their own transactions before those and profit from the price move that will happen once the original transaction is confirmed.
Front Running Process Breakdown
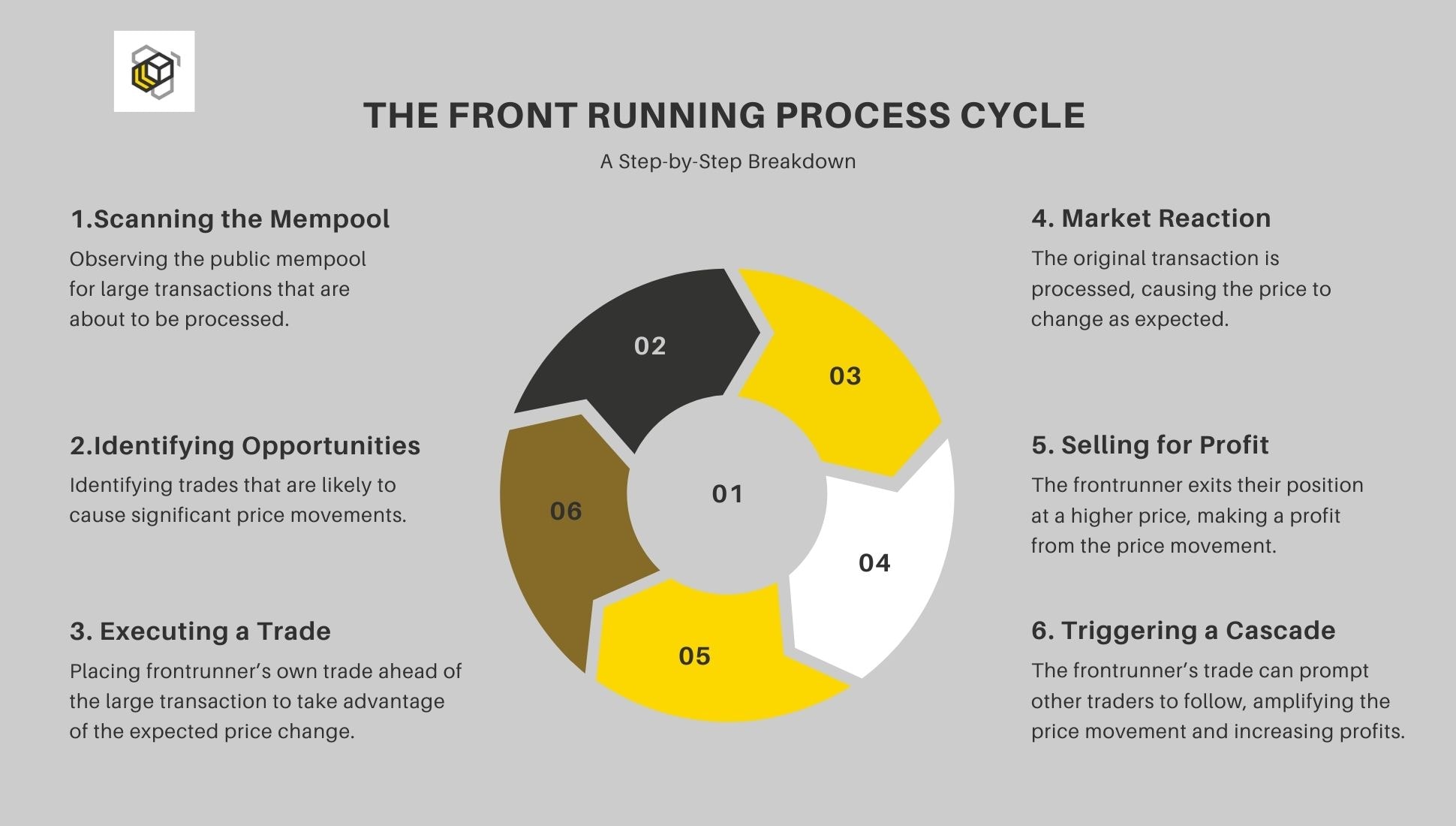
- Transaction Visibility: On decentralized platforms transactions are public in the mempool before they’re confirmed, front-runners can see upcoming trades.
- Opportunity Identification: Bots or miners look for large trades or price sensitive transactions in the mempool, such as big buy orders that will likely move the price.
- Trading: Once an opportunity is found, the front-runner places a trade that will benefit from the expected price move. For example, they buy an asset before a big buy order is processed and sell it once the market reacts.
- Transaction Finalization: The original order is completed, impacting the market as expected.
- Profit Realized: The front-runner sells their position at the new higher price and profits from the price move caused by the original trade. This often results in slippage, the original trader gets a worse price because of the front-runner’s trade.
- Cycle repeats: This happens over and over as front-runners monitor the mempool for new opportunities and profit from their knowledge of pending transactions.
Types of Front Running Attacks
Front running in crypto comes in many forms depending on the strategy and market:
- Trade Front Running – Exploiting large buy or sell orders on DEXs to profit from slippage.
- Arbitrage Front Running – Spotting price differences across platforms and trading before others can.
- Liquidation Front Running – Front-running DeFi liquidations by knowing when collateralized positions will be liquidated.
- NFT Front Running – Buying NFTs before a price spike based on mempool transactions.
These are all part of a broader phenomenon called Maximal Extractable Value (MEV) that affects the entire blockchain ecosystem.
What is MEV (Maximal Extractable Value)?
Maximal Extractable Value (MEV) is the extra profit miners or validators can make by changing the order or inclusion of transactions in a block. It includes several techniques, front running is one of them.
- Sandwich Attacks: Attackers buy before a big buy order in the mempool, moves the price up and then sell at the higher price after the original order is executed.
- Back Running – Traders watch for big trades and trade on the move. For example, if a big sell off sends prices down, they sell their positions before the market stabilizes.
- Displacement Front Running – Attackers flood the network with high fee transactions that fail. By doing this they push other transactions aside and get theirs in first.
- DEX Arbitrage – Bots scan different DEXs for price differences. When they find a financial asset cheaper on one and more expensive on another they buy low and sell high, causing price distortions.
MEV messes with market fairness and increases transaction costs and is a risk for crypto startups and their users.
How does Front Running affect Crypto Startups?
For crypto startups, front running can cause serious financial and reputational damage, especially when insider advance knowledge of future trades is used. Like established financial ecosystem, where brokerage firms use non-public information to trade ahead of clients, crypto front runners use public transaction information in the mempool. This can result in:
- Liquidity Drain: Market makers lose when front runners profit from price inefficiencies of large client orders and create temporary liquidity imbalances.
- Slippage Issues: Retail traders get worse prices, less people participate as trades are executed at worse prices because of front running.
- DeFi Risks – Bad actors take advantage of decentralized exchanges (DEXs) and automated market makers (AMMs) by spotting upcoming trades and influencing token prices before they go public.
- Trust and Reputation – If a crypto project becomes known for front-running issues, investors may think twice before getting involved—just like how insider trading scandals shake confidence in established financial ecosystem.
These challenges highlight why crypto projects need strong protections against front-running tactics.
How to Prevent Front Running
Crypto projects can avoid front-running risks through several ways, just like financial markets use trade surveillance technology to detect manipulation:
- Private Transactions – Solutions like Flashbots allow transactions to be submitted privately, so they don’t show up in the mempool. This is like how brokerages keep client orders confidential.
- Commit-Reveal Schemes – By delaying the reveal of transaction details until after execution, this method reduces the chance of front running. It’s like how index funds are transparent but keep sensitive trading info private.
- Batching – Bundling transactions together makes it harder for attackers to pick off individual trades. Like block trading in traditional finance where big orders are executed to minimize market impact.
- L2 Scaling: Moving transactions off-chain keeps them out of the public eye, so frontrunners can’t exploit them, just like executing trades through unmonitored accounts.
- Slippage Tolerance Settings: Allowing users to set slippage tolerance minimizes the impact of front running, protects traders from price movements caused by large orders or manipulation.
What is Flashbots and How does it Prevent MEV Exploits?

Flashbots is a tool to mitigate Maximal Extractable Value (MEV by providing an off-chain transaction relay. This allows traders to send private transactions directly to miners, without going through the public mempool and front running.
- Transaction Reordering Prevention: Flashbots prevents miners from reordering transactions within blocks, so trades are executed fairly without frontrunners exploiting prior non public knowledge, just like exchanges monitor for illegal stock price manipulation.
- Better Execution Pricing: By using Flashbots users get better prices for their trades, free from front runners, just like brokers get the best execution for their clients and avoid price inflation from pre-hedging.
- Better Market Efficiency: Flashbots reduces MEV, making the market more efficient and fair. It’s similar to trade reconstruction tools in traditional markets, ensuring transparency and preventing unfair practices like insider trading and pre-hedging.
How Smart Contract Audits can Help Reduce Front Running Risks?
Smart contract vulnerabilities are a big risk for crypto startups, just like execution flaws in traditional markets are exploited by insiders. Smart contract audits are crucial to identify and fix these issues. Here’s how:
- Execution Flaws: In both crypto and traditional markets, poor execution is a target for manipulation. If a smart contract is not designed properly, it can be exploited by frontrunners looking for weaknesses. An audit will spot these flaws and ensure future transactions are processed securely.
- Gas Optimization: Just like unmonitored accounts in the stock market can be exploited, inefficient smart contracts can attract unwanted attention from bad actors. By optimizing gas, audits prevent high fees and inefficient transactions that will attract frontrunners.
- MEV Testing: MEV attacks like sandwich attacks can harm your project. Audits test smart contracts to make sure they are MEV resistant, so you have a defense against potential exploits and fair trading for all parties involved.
By addressing these issues upfront, smart contract audits is an essential security layer, protecting your crypto project from security risks and building trust with users.
Best Tools for MEV Protection
Here are some tools to mitigate front running in crypto:
- Flashbots: Prevents mempool transaction leaks by sending private transactions directly to miners, so they are hidden from bots and attackers.
- CowSwap: Uses batch auctions to reduce MEV, so prices are less likely to be manipulated by frontrunners.
- Shielded Transactions: Aztec Network and similar protocols provide extra privacy for transactions, so sensitive information doesn’t leak before execution.
- Custom RPC Relays: Sending transactions directly to validators instead of broadcasting them publicly provides an extra layer of protection, just like how broker-dealers use proprietary information in trading desks to execute trades without tipping off the market.
While these tools are good, a bespoke approach to security is key for blockchain startups. The expertise to adapt these tools to your specific needs is critical for a secure and profitable environment for founders and users.
Takeaways
Front running is a big problem in traditional finance and crypto. Whether it’s individual brokers in traditional markets using nonpublic information about a client’s trade or automated bots in DeFi exploiting block transactions, it’s the same result—manipulated markets and unfair advantages. In traditional finance front running is illegal, often classified as securities fraud and can get you serious consequences from the Exchange Commission.
In crypto the transparency of market indexes and underlying securities on decentralized exchanges creates new challenges. But there are ways to fight back. Tools like Flashbots, commit-reveal schemes and transaction batching can help prevent index front running and illegal practices that exploit the mempool. Smart contract audits also make sure projects are not manipulable.
Ultimately, it’s the responsibility of crypto startups and projects to protect their users and themselves. By implementing the right tools, they can reduce risks, prevent market manipulation, and ensure a fairer trading environment.



